Understanding the Essentials of Security Audits for Small Businesses
In today’s digital age, small businesses are prime cyberattack targets. With the rise of new hacks and viruses developed daily, ensuring the security of your Canadian business’s digital infrastructure is critical. This is where security audits come in. They can be considered a comprehensive checkup of your IT infrastructure, designed to identify vulnerabilities and potential threats before they become a reality.
Read on to learn about the essentials of security audits for your small businesses and why they’re so important in the landscape of growing cyber risks in Canada.
The Evolving Cyber Threat Landscape
The digital realm presents small businesses with both opportunities and challenges. While technological advancements have revolutionized operations, they’ve also expanded the attack surface for cybercriminals. From ransomware attacks to phishing scams, criminals are developing increasingly sophisticated techniques to exploit vulnerabilities in business networks. In such a scenario, dynamic measures are essential to reduce risks and safeguard sensitive data.
Importance of Security Audits
Security audits are a foundational pillar of robust cybersecurity strategies for small businesses. These assessments provide comprehensive insights into the strengths and weaknesses of your digital infrastructure, enabling you to identify vulnerabilities before cyber threats exploit them. By conducting regular security audits, you can stay one step ahead of potential breaches, ensuring continuous protection of critical assets and sensitive information.
Benefits of Security Audits
Security audits help identify weaknesses, improve security measures, and demonstrate a commitment to protecting sensitive information. This leads to the long-term success of your business. Here are a few ways how security audits can help your small business.
Continuous Monitoring and Maintenance
Security is not a one-time job but rather an ongoing commitment. In addition to periodic security audits, continuous monitoring and maintenance services keep your digital infrastructure secure round-the-clock. This ensures that your business remains resilient against emerging cyber threats, allowing you to focus on driving growth and innovation without compromising on security.
Ensuring Regulatory Compliance
For small businesses operating in Canada, regulatory compliance regarding data security is non-negotiable. With stringent regulations such as the Personal Information Protection and Electronic Documents Act (PIPEDA) in place, businesses must implement robust security measures to protect customer data. Security audits help you identify compliance gaps and provide actionable recommendations to ensure adherence to regulatory requirements.
Comprehensive Evaluation of Security Measures During a security audit, skilled technicians thoroughly evaluate your business’s security measures. This evaluation includes assessing network configurations, firewall settings, access controls, and data encryption protocols. Scrutinizing each component of your digital ecosystem helps them better understand your security posture, enabling them to pinpoint areas that require immediate attention.
Identifying Vulnerabilities and Risks
One of the primary objectives of a security audit is to identify vulnerabilities and potential risks within your IT infrastructure. Whether it’s outdated software, misconfigured systems, or inadequate access controls, experts in the field can meticulously analyze every aspect of your network to uncover potential security gaps. By identifying these vulnerabilities early on, you can take proactive measures to reduce risks and fortify your defenses against cyber threats.
Tailored Recommendations and Strategies
Following a comprehensive security audit, you will get tailored recommendations and remediation strategies to address identified vulnerabilities effectively. Whether implementing multi-factor authentication, updating software patches, or enhancing employee training programs, you can develop a customized action plan that aligns with your business objectives and security goals.
Steps to a Successful Small Business Security Audit
To conduct a successful security audit for your small business, following a series of key steps is crucial to safeguard your organization’s assets, data, and systems effectively. Below are the vital actions necessary for a successful small business security audit:
● Establish Clear Goals and Scope: Start by defining the objectives and scope of your security audit, outlining what aspects of your business you aim to assess and improve, such as network security, data protection, or compliance with regulations.
● Build a Competent Audit Team: Form a team comprising internal IT professionals, cybersecurity experts, or external consultants with the requisite skills and knowledge to effectively evaluate your business’s security posture.
● Inventory Assets and Data: Develop a comprehensive inventory of your business’s assets and data, including hardware, software, sensitive information, and intellectual property, to determine what requires safeguarding.
● Thorough Risk Evaluation: Conduct a meticulous risk assessment to identify potential security threats and vulnerabilities, both internal and external, and assess their possible impact on your business operations.
● Scrutinize Current Policies and Practices: Review existing security policies, password protocols, access controls, data backup procedures, and incident response plans to pinpoint deficiencies or gaps in your security framework.
● Employ Vulnerability Scans: Utilize vulnerability scanning tools to detect weaknesses in your network and systems, promptly addressing any vulnerabilities that malicious actors could exploit.
● Ensure Regulatory Compliance: Evaluate your adherence to industry regulations and legal requirements, ensuring that your security practices align with the set standards to mitigate legal risks.
● Foster Employee Awareness: Measure the level of security awareness among your staff and provide training to enhance their understanding of security best practices, such as identifying phishing attempts and maintaining secure passwords.
● Prioritize Data Protection: Assess how your business handles sensitive customer and employee data, implementing robust data encryption, access controls, and data retention policies to safeguard confidentiality.
● Comprehensive Documentation: Document audit findings meticulously, generating a report delineating identified vulnerabilities, recommended enhancements, and an actionable plan for building security measures.
● Swift Remediation Implementation: Take immediate steps to rectify identified vulnerabilities and weaknesses, incorporate new security measures, update policies, and conduct employee training as necessary.
● Continuous Monitoring and Adaptation: Recognize that security is an ongoing process, requiring constant monitoring and adjustment of security measures to address emerging threats and technological advancements.
● Periodic Audit Reviews: Schedule regular follow-up audits to evaluate the efficacy of implemented security improvements and ensure the sustained security of your small business operations.
By following these essential steps, you can gain valuable insights into your security posture. Security audits empower you to proactively identify and address vulnerabilities, reducing risks and safeguarding your critical assets, data, and systems.
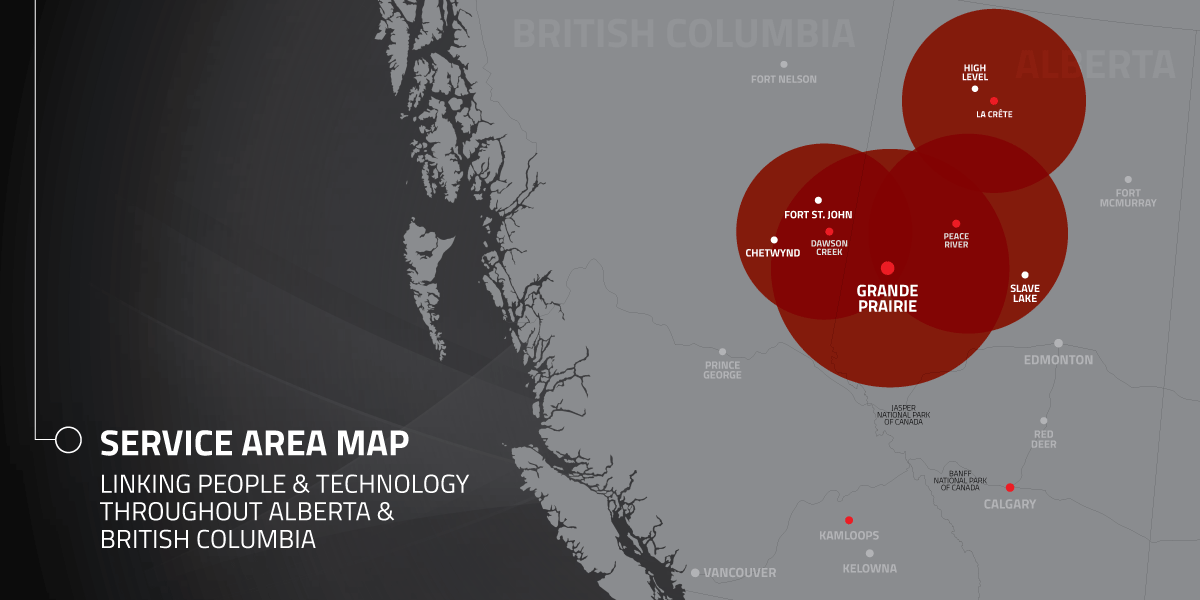
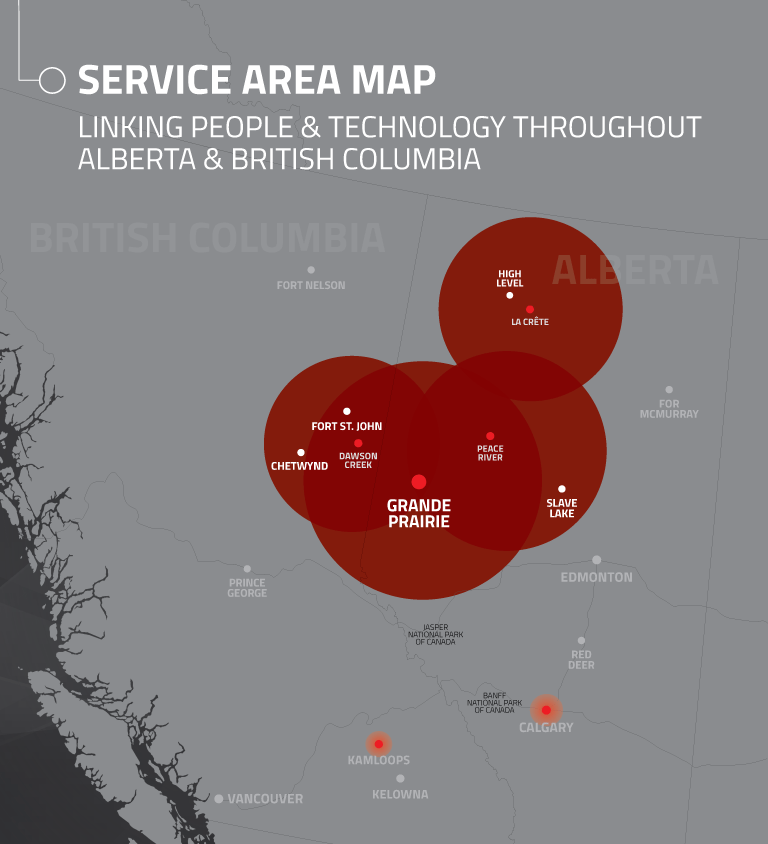
So how do you get started? Reach out to Hi-Tech Business Systems, who can solve all your tech problems, allowing you to focus on your business. Contact us to learn more about our services.